
PC users completely rely on anti-spyware software program for their complete security and protection. But what if the anti-spyware protection tool is itself malicious? It is the case with Internet Security which is identified as a fake rogue anti-spyware software program which is purposely designed to extort money from innocent PC users. Although it's entry to targeted users computer is without their consent or knowledge however some of the common traits clearly signifies it's presence within your computer. It throws number of errors and alert messages that urges user to believe that their PC is under threat of highly risky and notorious malware. Thus compels you to purchase the licensed version of the software program to ensure complete removal of the threat. But under no circumstance you are suggested to waste your money in buying the bogus software. Similar to the alerts the software program is also unrealistic and is a trick of hackers to extract money from naïve users. Therefore instead of buying the product you are supposed to look for genuine methods to delete Internet Security safely.
Automatic Internet Security Removal
Although manual steps to remove Trojan.Agent.kro is available however it is strictly advised to go for the alternative option of Automatic Internet Security Removal Tool if you are not technically sound enough. The automatic removal tool comes with an easy to use interface which does not require user to be technically strong for it's installation and execution.
User Guide: How To Use The Software
Step 1:
Once the Download Now Button shown above is clicked, one of the below given dialog box depending on the browser being used would be displayed from here save file option is to be selected for the software to be downloaded. After this run the setup, by double clicking it and then you can proceed with the installation step as instructed by the program, as shown in the image below.
Step 2:
Once the installation process is completed, program icon could be found on the desktop from where it can be executed.
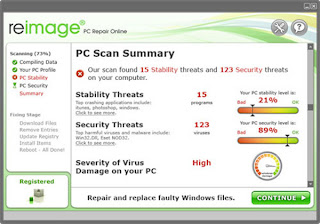
Step 3:
Upon launching the software & starting the scan process all infections that exist in the system could be revealed as in shown in the image below and can be cleaned from there easily.
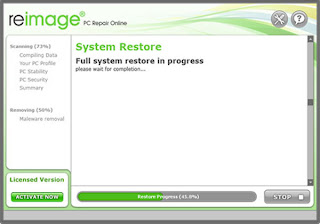
Step 4:
The Software provides lots of security measures and protection level settings that can make your computer completely protected from all kinds of PC threats.


No comments:
Post a Comment