McAfee recently recognized VSkimmer as one of the insidious Trojan for sale highly prone to attack devices associated with Point of Sale(POS), credit card channels, and other peripheral devices running any version of Windows OS. These little gem of malicious software are built for the explicit purpose of collecting banking credentials and credit label information and sending them to the cyberpunks sitting remotely on the control server. In most of the cases it has been seen that user remains unfamiliar to such kind of threat infection or came to know about it very late. In order to avoid such kind of financial scams it is highly recommended to remove VSkimmer using an advance and powerful tool.
Automatic VSkimmer Removal
Although manual steps to remove Trojan.Agent.kro is available however it is strictly advised to go for the alternative option of Automatic VSkimmer Removal Tool if you are not technically sound enough. The automatic removal tool comes with an easy to use interface which does not require user to be technically strong for it's installation and execution.
User Guide: How To Use The Software
Step 1:
Once the Download Now Button shown above is clicked, one of the below given dialog box depending on the browser being used would be displayed from here save file option is to be selected for the software to be downloaded. After this run the setup, by double clicking it and then you can proceed with the installation step as instructed by the program, as shown in the image below.
Once the installation process is completed, program icon could be found on the desktop from where it can be executed.
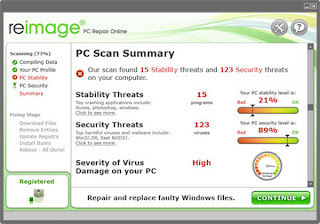
Step 3:
Upon launching the software & starting the scan process all infections that exist in the system could be revealed as in shown in the image below and can be cleaned from there easily.
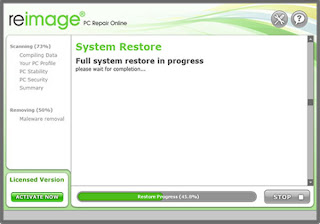
Step 4:
The Software provides lots of security measures and protection level settings that can make your computer completely protected from all kinds of PC threats.


No comments:
Post a Comment